By:
Kayzad Vanskuiwalla, Director – Threat Hunting and Intelligence, Securonix Threat Labs
Vikas Kataria, Technical Lead – Cloud, Securonix
This is the concluding article in a series of three blog posts on monitoring threats in cloud environments. In the first two blog posts, we spoke about the need for monitoring threats in the cloud and how insider threat prominently features as one of the key aspects to monitor.
In this final part we will discuss how cloud controls can be abused, using AWS as an example, because similar issues also plague other providers like Microsoft Azure, Google Cloud Platform, or Oracle Cloud Infrastructure. We will detail a few different scenarios around how particular controls can be misused and how to detect these using UEBA / machine learning or even threat hunting.
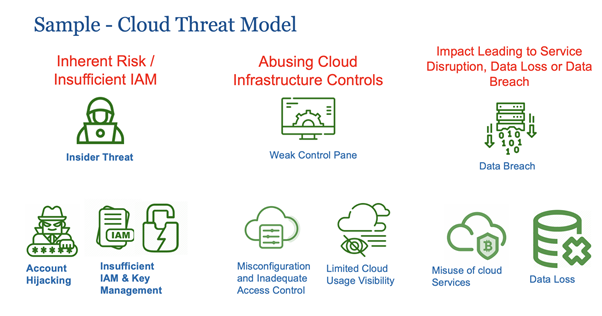
Below is a summary of what we will be covering in each section:
- Each section will talk about the relevant real world attacks as described under the CSA egregious 11 , a description of the scenario, and how you can detect that scenario using user entity behavior analytics / various hunting techniques.
- To start with we talk about insufficient IAM and the inherent risk / insufficient IAM scenarios related to accounts being misused or compromised. This includes authentication anomalies (like multifactor authentication being disabled) or users misusing or elevating their privileges / roles etc.
- This is followed by the section on detecting what can go wrong with the cloud infrastructure itself, i.e. abusing cloud infrastructure controls including modifying policies , ACLs (access control lists), unapproved operations on key vaults (keys that manage the encryption for all cloud services) as well as detecting signs of discovering accounts / services that can be misused / abused.
- The last section talks about the final impact leading to service disruption, data loss, or data breach around what can go wrong with these cloud services with service disruption affecting the organization. This varies from data loss (deletion / modification of encryption keys would mean all data is lost), data breach (Data is available to anyone across the internet in an unauthorized manner), abuse cloud services (services / instances are created to be used in a manner that wasn’t intended, like cryptomining).
Inherent Risk / Insufficient IAM
The risk in this scenario comes from accounts that have the ability to be misused or to elevate privileges, whether by a malicious insider or through compromised credentials. For more details around the types of insiders you should monitor you can reference our earlier blog post here.
Relevant Real World Attacks for Inherent Risk / Insufficient IAM
The scenarios of interest can be highlighted by the attack on Tesla, where attackers gained access to insecure or unprotected Infrastructure; Disney+, where attackers used compromised credentials; or Tesco, where third party providers failed to implement the right level of controls and secure images.
Risk Scenario: Account Compromise and Misuse
Organizations are using 100s of Saas applications on average which leverage multiple cloud services like IAM, infrastructure management, storage management, key management etc. to maintain those applications. Bring your own device (BYOD) is also still on the rise, and users are increasingly using their private devices to gain access to these applications, introducing further potential for account compromise. The amount of different accounts in use in combination with usage outside of the traditional perimeter and outside of the control of I.T. mean that account compromise and misuse have increased.
Detection Strategy: Continuous Monitoring – Inherent Risk
The key to detecting account misuse or compromised cloud credentials is to collect various relevant signals (or observables) for entities of interest. This can include privileged accounts, accounts with upcoming terminations, or other indicators of inherent risk like poor performance reviews etc. can be used for continuous monitoring via a watchlist.
We can focus on anomalies associated with these entities related to initial access indicating the use of compromised credentials or attempted privilege escalation:
- Detecting a rare country associated with where a user is authenticating from.
- Authentication events originating from two simultaneous locations (also called impossible travel or land speed anomalies).
Below is an example of a user authenticating from a rare country (Bulgaria) while authenticating simultaneously from the United States. The geolocation information can be enriched to detect these scenarios.
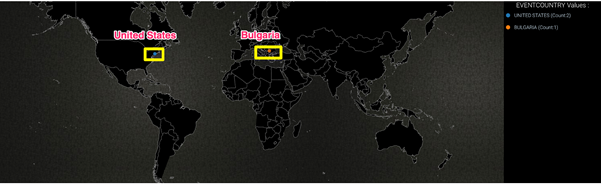
An event such as a rare country by itself may not be malicious / suspicious, however it can be used as a precursor to identifying scenarios of account compromise / account sharing.
Detection Technique: Relevant Use Cases to Detect Inherent Risk Include:
Rare country for SAML Token authentication
Flight risk / exiting risk behavior
Abuse Controls of Cloud Infrastructure / Cloud Objects
In this section we will cover scenarios related to privilege escalation as well as configurations modified on the cloud infrastructure.
Relevant Real World Attacks for Abuse Controls of Cloud Infrastructure / Cloud Objects:
The related scenario at Imperva where, due to a misconfiguration the server was made accessible from across the internet is an example of this scenario as well as the scenario with Dow Jones where data was exposed due to a misconfiguration. In these and other scenarios it was down to misconfigurations of specific services or lack of security controls that contributed to the underlying issue. S3 Ransomware is another aspect related to misuse of the KMS service.
Risk Scenario: Role-Based Privilege Misuse
In this scenario the organization didn’t globally enforce policies around the types of users / roles that were authorized to perform these privileged transactions.
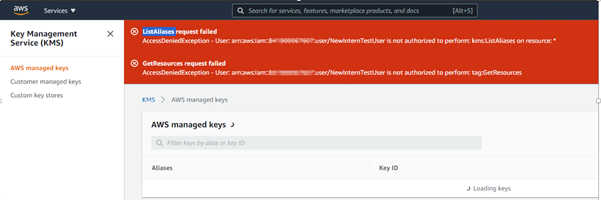
The user in this case unsuccessfully attempted to get a list of aliases / resources as seen below.
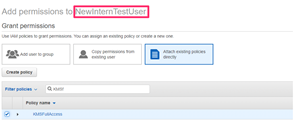
The user was therefore easily able to elevate their own privileges as shown below. The user NewInternTestUser now has additional privileges on KMS (key management) as well as administrative access.
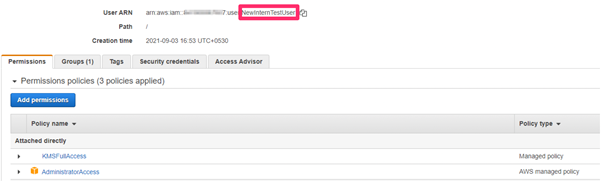
As shown below – the user NewInternTestUser now has additional privileges.
Risk Scenario: Modifying Permissions of AWS Cloud Instances
Once a malicious actor has elevated privileges, or has access to a group or role that can perform elevated transactions, there are a number of possible actions they can take that may negatively impact your organization.
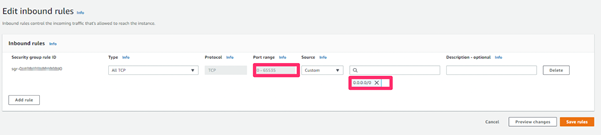
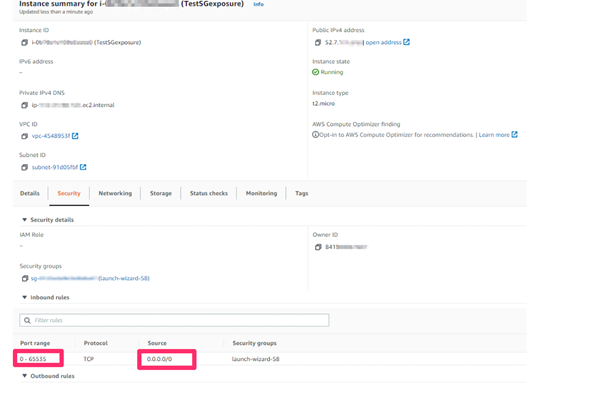
In the scenario we see in the screenshot below, the account used by the attacker was able to modify the permissions for an AWS instance to make it accessible by anyone on the internet. The account was able to modify permissions to allow traffic from any IP address (0.0.0.0/0) to any port (0-65535).
The attacker can now remotely gain access to this instance to cause considerable damage, for example by completely deleting the instance, or even leaking data contained in those instances. The attacker may also be able to maintain persistence, to gain access again at any time in the future.
Detection Strategy: Privilege Escalation
In this scenario continuous monitoring around the list of users that perform any privileged transactions as well as users that ideally should not be performing these actions should be grouped and monitored.
Grouping accounts similar in nature – admins, privileged accounts, service accounts, privileged hosts, general users would help with this type of detection.
A UEBA platform can dynamically build a cohesive group of entities based on specific criteria and thereby detect any cases of unauthorized activity compared to the rest of the peer population.
Identifying anomalous access patterns on the host in question and the set of entities that can perform privileged actions on the host would also be of interest in this scenario.
Relevant Use Cases to Detect Abuse Controls of Cloud Infrastructure / Cloud Objects Include:
Rare Account Creating or Modifying Identity Policy
Recon Activity Detected on Cloud Computing Resource
Account modifying ACL or Permissions of a cloud storage resource
Impact Leading to Service Disruption, Data Loss, or Data Breach
Relevant Real World Attacks for Impact
The scenarios of interest can be highlighted by the attack on Tesla – where attackers gained access to insecure or unprotected Infrastructure and led to S3 buckets being made publicly available as well as utilizing Kubernetes instances to mine cryptocurrency.
Risk Scenario: Modifying AWS S3 Bucket Access Permissions
One of the most critical aspects to monitor are related to storage objects (buckets on AWS) and the permissions associated with these objects. A user with elevated privileges can modify permissions and have the object accessed by anyone.
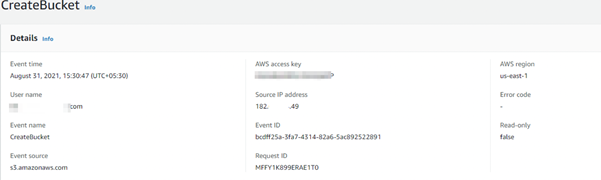
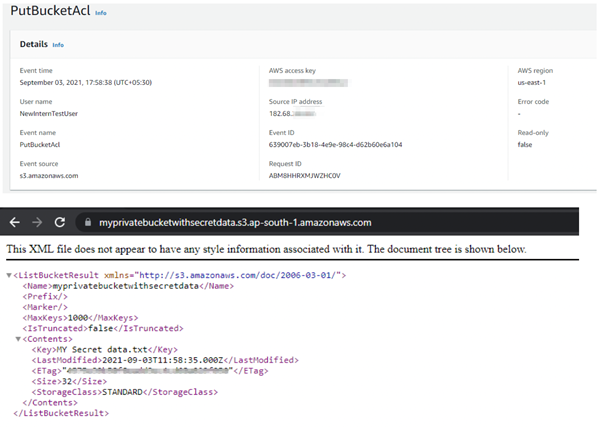
We start by observing an event to create a bucket. Here ideally the default doesn’t create a bucket that can be accessed publicly.
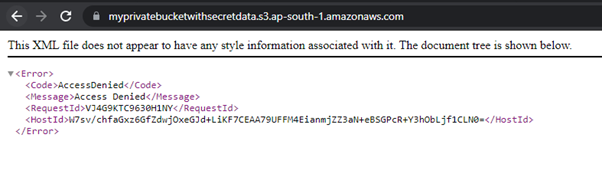
The image below shows an error generated when we tried to access this bucket.
Now we see a user that has elevated privileges modifies permissions for the bucket, making it publicly accessible.
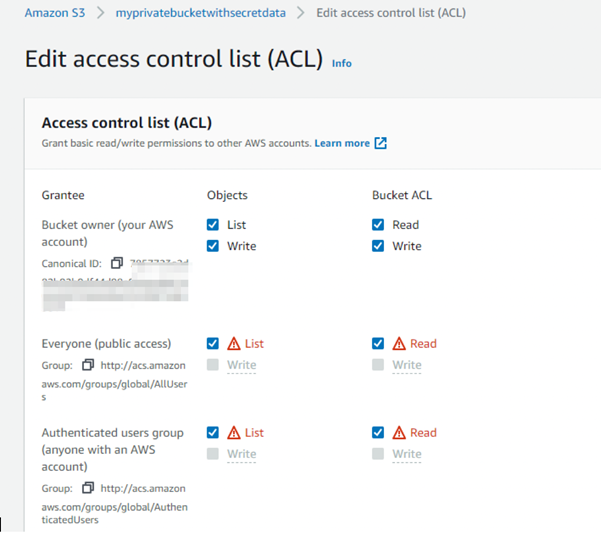
As can be seen below, the bucket is now accessible publicly and all information within the bucket is accessible as well.
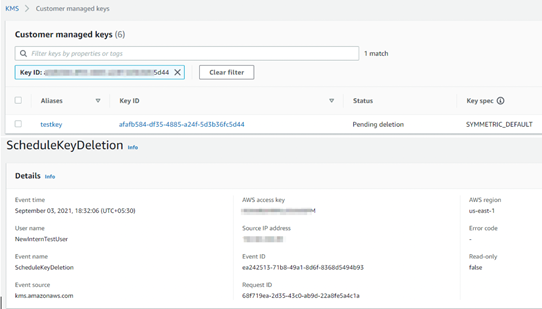
Risk Scenario: Deleting or Modifying Cryptographic Keys
Another important aspect to monitor is around the cryptographic keys used by various cloud services. A compromise or elevated privileges against the KMS (key management server) would mean that the data as well as services would be inaccessible.
In the example below, we can see that the key was intentionally deleted. This would cause all data and any services leveraging these keys to be made inaccessible.
Detection Strategy: Impact
While there are various signals that may help identify scenarios of impact, detections around modifying object permissions, roles, and deleting objects / keys should be monitored as well.
This can again be identified based on a peer grouping of types of objects (ones that should be accessed publicly – publicly available information) or any attempt to modify or delete keys that is abnormal compared to the object and entities performing this activity. A spike in object / instances deleted or even created should also be monitored for detecting additional artifacts of compromise.
Relevant Use Cases to Detect Impact:
Cloud Storage observed with public access
Customer master keys Disabled or Scheduled for Deletion
Conclusion – Sample Cloud Threat Model – Putting it All Together
We went over various aspects of cloud controls and how they can be misused, leading to a data breach, data loss, or even entire instances being spun and misused.
They key here is to bucket various anomalies (signals / observables) into different aspects such as:
- Entity performing the activity (admins / privileged accounts / users )
- Identify and continuously monitor non-technical feeds for insider threats to prioritize inherent risk.
- For the entities watchlisted above, focus on signs of:
- Account compromise
- Privilege escalation
- Defense evasion (disabling logging / existing controls)
- Ultimately monitor for an impact related to:
- Data breach (unauthorized data access)
- Data loss (deleted / modified / disabled keys, instances or objects)
- Misuse of cloud services (creating and using instances or objects beyond the intended official purpose)
In most cases the inherent risk along with intent (from an insider threat or potential compromised account) that is misusing or abusing controls can be used to proactively prevent the consequence of impact discussed. This includes an example or a sample threat model with the various scenarios we discussed in these blog posts but there are over 100 others that can be monitored and available as part of Securonix Cloud Detections and are constantly evolving with the advancing threat landscape.
With this approach Securonix was able to detect the following purple team test conducted with a random sample set of controls misused in a live environment with AWS Cloud Trail and Guard Duty enabled.
| Use Case Name | MITRE Indicator | Theme | Detected on Guard Duty | Detected via Securonix use cases on raw Cloud Trail logs |
| Root User Activity Detected on Cloud Instance | Valid Accounts | Privilege Misuse | Yes | Yes |
| MFA Disabled for Root User Account | Valid Accounts | Privilege Misuse – Defense Evasion | No | Yes |
| Customer master keys Disabled or Scheduled for Deletion | Data Destruction | Data Loss | No | Yes |
| Cloud Storage observed with public access | Data from Cloud Storage Object | Data Breach | Yes | Yes |
| Disabling or Modifying Audit Logs on Cloud Platforms | Delete Cloud Logs | Privilege Misuse – Defense Evasion | Yes | Yes |
| Possible Exfiltration Activity Detected | Transfer Data to Cloud Account | Information Disclosure – Exfiltration | No | Yes |
| Account modifying ACL or Permissions of a cloud storage resource | Cloud Service Discovery | Privilege Misuse | No | Yes |
| Rare security group changes on cloud infrastructure by account | Privilege Escalation | Misconfiguration or Inadequate change control | No | Yes |
| Rare privilege escalation through IAM instance profile | Privilege Escalation | Insufficient IAM Management | No | Yes |
| Rare Account Manipulating Customer Managed IAM Policy | Privilege Escalation | Insufficient IAM Management | No | Yes |
| Possible Cryptomining Attack Detected | Resource Hijacking | Cloud Infrastructure Abuse | No | Yes |
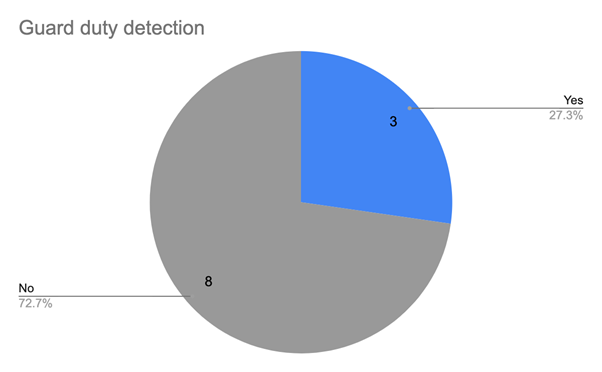
The table below shows some of the scenarios that Securonix provides coverage for using raw cloud audit data, split into the focus areas mentioned above.
Relevant use cases by focus areas
| Inherent Risk / Insufficient IAM | Misconfiguration and Inadequate Access Control | Data Breach / Data Loss / Misuse Cloud Services |
| MFA Disabled for Root User Account
Flight risk / exiting risk behavior Users/ Contractors with upcoming termination dates |
Rare Account Creating or Modifying Identity Policy Recon Activity Detected on Cloud Computing Resource Account modifying ACL or Permissions of a cloud storage resource Rare Account Creating Accesskey Rare cloud storage discovery activity from Account Account Discovery – Account lists all the AWS accounts in the region Unusual number of Key Vault operations |
Possible Exfiltration Activity Detected
|