- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Augusto Barros, VP, Cybersecurity Evangelist, Securonix
Securonix aligns with the MITRE ATT&CK framework, not just for generating individual alerts but to leverage ATT&CK chains to track, understand, and address the full scope of an attack. The MITRE ATT&CK framework has obvious value for addressing the external threats you read about all the time, but what about insider threats? To answer this question, it’s useful to understand how insider threats differ from external threats and how those differences apply to the framework.
Insider Threats Are Evolving
Insider threats encompass any risk posed by employees, contractors, or anyone with authorized access to sensitive data. They include data theft, misuse of access privileges, sabotage, and fraudulent activity that puts the organization’s reputation and brand at risk. According to a 2019 security survey by Forrester, about 25% of today’s security breaches were the result of internal incidents, with another 21% involving business partners or suppliers.
Only half of insider threat agents are malicious, according to Forrester. The rest are either complacent, such as when an employee enables others to harm the organization, or ignorant, where the user doesn’t realize the dangers of their actions.
While insider threats are not as numerous as external threats, their potential for harm is greater, thanks to the knowledge and access insiders have to an organization’s most valuable data sources.
The insider threat landscape has evolved over time with new types of actors, such as nation states and supply chain partners, and new risks that come from the growth of remote work and the cloud. Today, cloud service employees may have access to your cloud-based systems or vendor employees to your organization’s infrastructure. Tracking sensitive data on remote devices is also a lot more challenging than doing so on the corporate network.
Insider threat techniques have evolved as well. Securonix’s 2020 Insider Threat Report analyzed 300 real incidents across eight industries and found that leveraging cloud resources, such as forwarding emails to a personal email account or transferring sensitive data to a personal cloud storage and collaboration service, such as Dropbox, Box, or Office 365, were the most common insider threat techniques today.
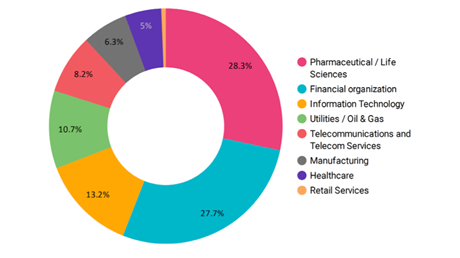
The types of threats that are most harmful differ by industry. Pharmaceutical firms had the highest percentage of incidents, with theft of intellectual property the most damaging. Financial firms, with the second highest percentage, were particularly vulnerable to insider fraud, while critical infrastructure providers tended to be most concerned with sabotage.
The MITRE ATT&CK Framework
The MITRE ATT&CK framework is both a model and a published knowledgebase of attack tactics and techniques. Tactics describe general attack steps, such as reconnaissance, privilege escalation, and command and control, while techniques are the known specific actions that fit into the tactic categories, such as operating system credential dumping or a man-in-the-middle attack.
When it comes to insider attacks, it’s important to understand that many of the attack tactics and techniques described by the framework are not applicable. For example, the preliminary steps that external hackers use to gain access to the organization’s IT environment typically don’t apply to insiders, since they already have access to the network and many of its systems. As they gain more privileges and access, outsiders start to look more like insiders.
As you can see in the graphic below, insiders usually skip the first few steps in a MITRE attack chain and go directly to discovery, privilege escalation, lateral movement, and other techniques for accessing and transferring data.
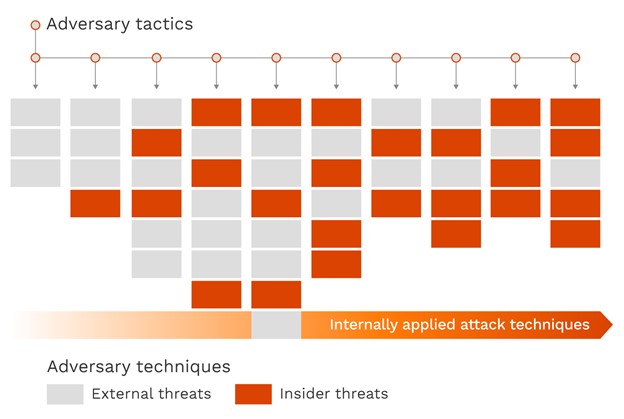
However, while a large portion of the MITRE ATT&CK framework’s content is geared toward external attacks, its structure and language are neutral and very useful for addressing and communicating insider attack information to relevant parties.
The framework is also useful for identifying data sources used to detect attacks. Each technique lists relevant data sources that can help with the attack detection, regardless of whether the threat is external or internal. For insider attacks, application and authentication logs are potentially as or more useful and relevant than telemetry from EDR tools, which are device centric and rarely have any knowledge of user identity.
The framework can also help security teams identify content, such as rules, machine learning models, and signatures they can use to prevent, detect, or contain insider attacks and understand where they need to develop their content further. Finally, the framework’s language and structure are very useful for documenting and standardizing incident response steps and analyzing lessons learned.
Securonix and Insider Attacks
Thanks to its alignment with the MITRE ATT&CK framework and its user and entity behavior analytics (UEBA), Securonix can help you fill in your organization’s own specific content gaps. For example, if you’re concerned about insider use of data encryption for exfiltration, you can enable content related to MITRE ATT&CK technique T1486 (Data Encrypted for Impact) on Securonix to support detection and containment of these types of attacks.
Another great example is this real case of an insider attack and the actual steps taken. You can see that every step maps to an ATT&CK technique.
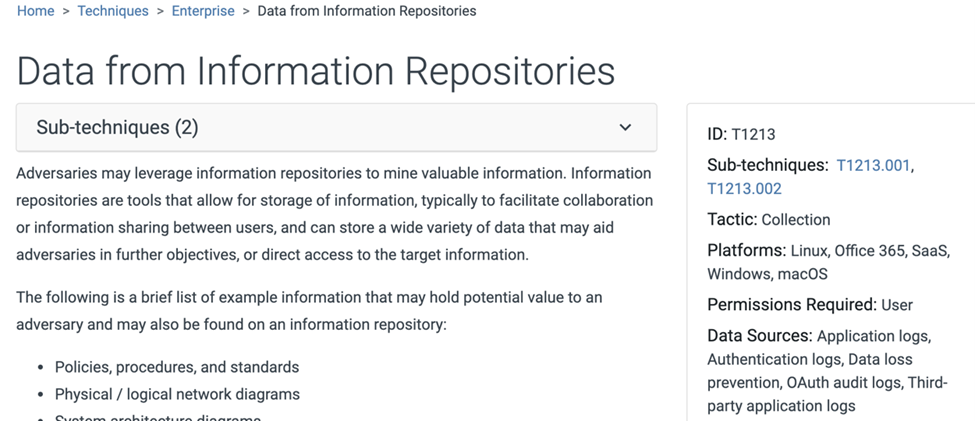
- Data from information repositories – Large number of sensitive XLS/DOC and AUTOCAD .DQG files copied from corporate Salesforce/Cloud drive (T1213)
- Data staged – Sensitive data copied to host (T1074)
- Archive collected data – Password-protected ZIP file containing collected files created on host (T1560)
- Obfuscated files or information: steganography – StegoMagic tool used to embed the sensitive data into a .bmp image file (T1027.003)
- Multi-hop proxy – Connection to TOR exit node (T1090.003)
- Exfiltration over alternative protocol – Image files with sensitive data sent to personal email @qq.com (T1048)
So how do you use Securonix and the MITRE ATT&CK framework together to address insider attacks in your organization? You need to prioritize the techniques that apply both to insider attacks and your IT environment. You must also incorporate other useful content not contained in the framework. For example, there are human factors related to insider flight risk, such as a bad performance review, that are not described anywhere in the framework. Securonix lets you build watchlists of these potential insiders. A lot of fraud techniques involving insider business applications are also not visible in MITRE ATT&CK, but can be detected by Securonix.
Behavioral context and Securonix’s UEBA capabilities are invaluable for insider threat detection. Securonix can build that user context over time and alert you to anomalies, such as a user on a watchlist suddenly making an unusually large outbound data transfer vs. an employee not on a watchlist who always makes large transfers as part of their job. If a user typically accesses certain systems but suddenly starts accessing a different set of systems, or systems not typically accessed by their peer group, that’s an anomaly worth further examination. Securonix provides an insider threat content package that tracks activities such as credential sharing, data egress, data snooping, and expense fraud and includes a lot of prebuilt content.
The MITRE ATT&CK framework, watchlists, and UEBA make a very powerful combination for preventing and stopping just about every type of insider attack.
For more information on attacks, the MITRE ATT&CK framework and Securonix, check out the recording of this seminar.







