- Why Securonix?
- Products
-
- Overview
- Securonix Cloud Advantage
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Resources
- Partners
- Company
- Blog
Threat Research
Introduction
A newly discovered passive backdoor appears to be attributed to Red Menshen, a threat actor group based out of China. In a recent case study by PwC, it’s clear that the threat actors have been leveraging BPFDoor for quite some time, and both the scope and details as to how the backdoor functions are just now coming to light.
According to an analysis by the Securonix Threat Research team, it would appear that there are several variations of the backdoor. However, all have the same goal, to allow C2 communication by a remote attacker.
Attack Chain and Scope
According to PwC, earlier targets appeared mostly in telecom, government, education, and logistics. Today, as more information comes to light, it’s possible that the target scope has spread to other sectors, and BPFDoor has been around much longer than initially speculated. In some cases, the backdoor may have been integrated into some systems for up to five years.
As with many remote access tools, BPFDoor would typically be implanted into its target during the post-exploitation phase of an attack. This would require a vulnerable server to allow the attackers initial access before implementing the tool. An example of this would be the popular Log4Shell vulnerability from late last year.
Target systems for the backdoor would be purely Linux-based. During our analysis, we found samples for both x86 and x64-based systems and the Solaris SPARC platform.
Behavioral Analysis
Affected systems with BPFDoor allow a remote attacker to access the system using a wide range of protocols. It supports TCP, UDP, and ICMP for data communication and relies on the BPF packet filter (hence the name) for establishing communication. This advantage is that it allows the backdoor to establish socket communication through existing open ports. For example, suppose only port 80 is allowed through the local firewall, and the server has a web app running on port 80. The backdoor can still establish and maintain its C2 protocols through that open port without affecting the original application.
This can make the backdoor very difficult to detect as it does not need to open any new ports on the target host, so it likely went undetected for as long as it did.
BPFDoor also has built-in functions which allow the attacker to set a password, thus encrypting the communication between host and target. However, this functionality was not always present in every sample we analyzed.
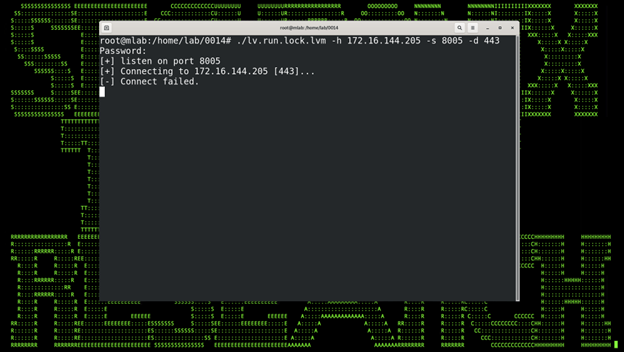
Figure 0
The backdoor will present a challenge password to the listening host if the backdoor can connect. Finally, the handshake is complete, and C2 is established if the password is correct.
When it was rerun with a Netcat listener on the target host, we get a successful connection:
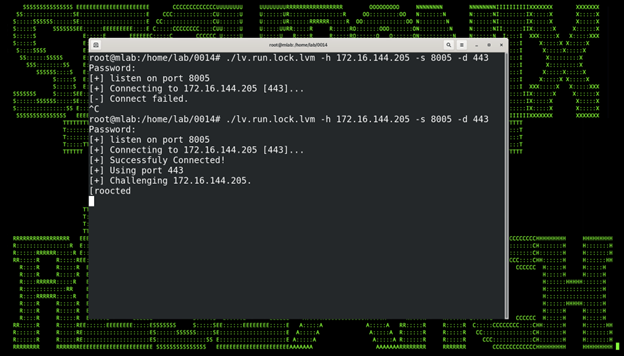
Figure 1: Victim
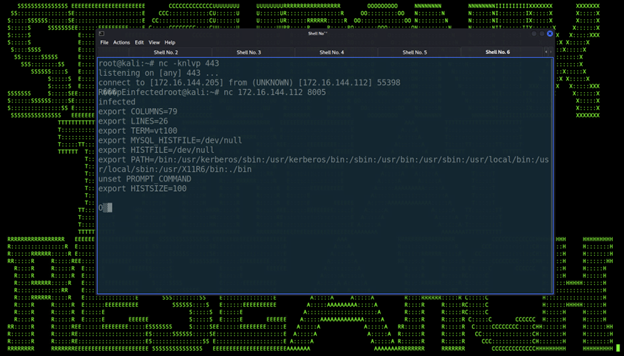
Figure 2: Attacker
Technical Analysis
Of the dozen samples we analyzed from different sources, we noticed quite a few technical variations in each binary. As we mentioned previously, BPFDoor is intended for Linux targets and is available across multiple CPU architectures, including x86, x64, and SPARC platforms.
Each sample we analyzed was a Linux executable ELF file having a unique name. For example, one particular analyzed sample’s binary data can be seen in figure 3:
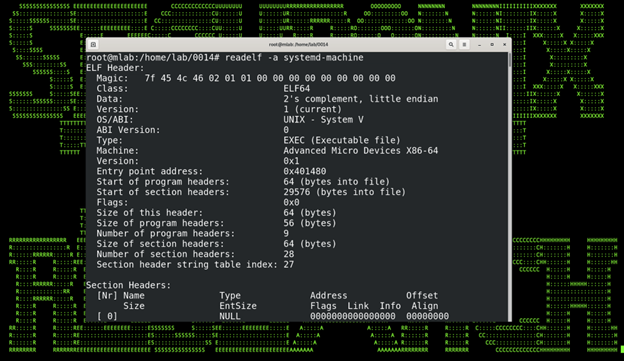
Figure 3
Opening one of the random samples will occasionally provide us with function names that are clearly defined. This is great because it provides high-level information about BPFDoor’s overall functionality. Some particularly interesting function names are getshell, getpasswd, icmpcmd, shell, set_proc_name, and sendcmd to name a few.
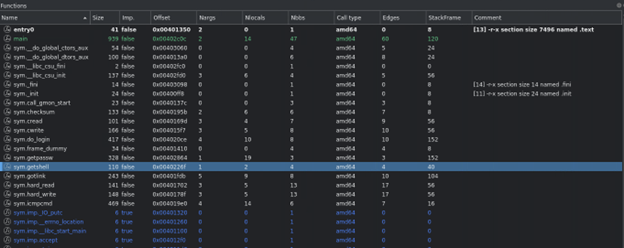
Figure 4
Some of the samples we analyzed were more obfuscated at a binary level than others. In some cases, strings were broken out into individual variables and hex encoded. Once decoded, some individual commands can be seen. This particular sample writes to the /var/lock directory.
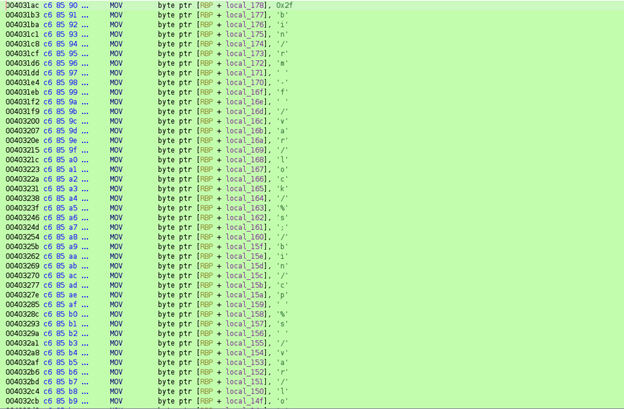
Figure 5
After execution, the backdoor will clear the “environ” information on the Linux host. This data is typically associated with a process PID and located in /proc/[pid]/environ. Once the data is wiped, the backdoor will fill it with predefined environmental variables. This ensures the attacker will have everything they need to perform their functions.
Figure 6
Upon execution, the backdoor will masquerade as a legitimate-looking system process in some cases. This is because it pulls from a random set of predefined processes. This helps it blend in better when viewing or monitoring processes on the Linux host.
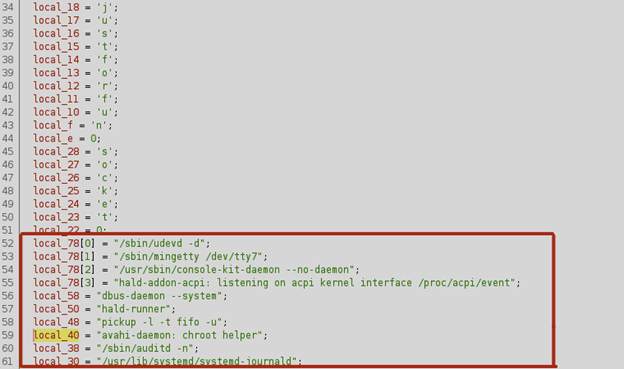
Figure 7
In a nutshell, of all the samples we analyzed, we were able to track a few consistent patterns, such as the directories that the backdoor would interact with and some system commands such as iptables. When it comes to detections, we will be leveraging some of these patterns to look for signs of compromise.
Securonix Recommendations and Mitigations
Given the stealthy nature of BPFDoor, we recommend that Securonix customers scan their environment using the detections highlighted in the next section.
- Deploy antimalware software on Linux hosts and run aggressive scans.
- Monitor and baseline outbound network port communications for unusual spikes or unusual volume trends.
- Implement outbound geo-blocking rules on the firewall, and monitor denied firewall communications to suspicious countries.
Detections
Seeder Hunting Queries
- rg_functionality = “Unix / Linux / AIX” AND filename NOT NULL AND filename CONTAINS “haldrund.pid”
- rg_functionality = “Unix / Linux / AIX” AND deviceprocessname ENDS WITH “kdumpdb”
- rg_functionality = “Unix / Linux / AIX” AND deviceprocessname ENDS WITH “kdumpflush”
- rg_functionality = “Unix / Linux / AIX” AND resourcecustomfield5 NOT NULL AND resourcecustomfield5 CONTAINS “/bin/rm” AND resourcecustomfield5 CONTAINS “/bin/chmod” AND resourcecustomfield5 CONTAINS “/dev/shm/”
- rg_functionality = “Unix / Linux / AIX” AND resourcecustomfield5 CONTAINS “/dev/shm/”
- #iptables ports 42391-43391
- rg_functionality = “Unix / Linux / AIX” AND resourcecustomfield5 NOT NULL AND resourcecustomfield5 CONTAINS “iptables -t nat” AND resourcecustomfield5 CONTAINS “REDIRECT –to-ports 42”
- rg_functionality = “Unix / Linux / AIX” AND resourcecustomfield5 NOT NULL AND resourcecustomfield5 CONTAINS “iptables -t nat” AND resourcecustomfield5 CONTAINS “REDIRECT –to-ports 43”
Securonix detection policies will be updated by May 17th
Note: If you are an Autonomous Threat Sweeper subscriber, all of the above TTPs have been swept and a summary detection report will be shared with the recipients if its not already.
For the latest threat intelligence and updates please refer to our Github page that is updated daily. We also invite you to send your questions regarding critical security advisories to the Securonix Critical Intelligence Advisory team and look forward to being of assistance.
References
- [1] https://www.pwc.com/gx/en/issues/cybersecurity/cyber-threat-intelligence/cyber-year-in-retrospect/yir-cyber-threats-report-download.pdf
- [2] https://www.ibm.com/docs/en/qsip/7.4?topic=queries-berkeley-packet-filters
Analyzed Samples (SHA256):
93f4262fce8c6b4f8e239c35a0679fbbbb722141b95a5f2af53a2bcafe4edd1c
591198c234416c6ccbcea6967963ca2ca0f17050be7eed1602198308d9127c78
dc8346bf443b7b453f062740d8ae8d8d7ce879672810f4296158f90359dcae3a
c796fc66b655f6107eacbe78a37f0e8a2926f01fecebd9e68a66f0e261f91276
ac06771774538f33b0e95a92ae1a3e8aaf27e188b51700a03c14ca097af09cac
97a546c7d08ad34dfab74c9c8a96986c54768c592a8dae521ddcf612a84fb8cc
96e906128095dead57fdc9ce8688bb889166b67c9a1b8fdb93d7cff7f3836bb9
76bf736b25d5c9aaf6a84edd4e615796fffc338a893b49c120c0b4941ce37925
5faab159397964e630c4156f8852bcc6ee46df1cdd8be2a8d3f3d8e5980f3bb3
3a1b174f0c19c28f71e1babde01982c56d38d3672ea14d47c35ae3062e49b155
5b2a079690efb5f4e0944353dd883303ffd6bab4aad1f0c88b49a76ddcb28ee9
5faab159397964e630c4156f8852bcc6ee46df1cdd8be2a8d3f3d8e5980f3bb3
599ae527f10ddb4625687748b7d3734ee51673b664f2e5d0346e64f85e185683
144526d30ae747982079d5d340d1ff116a7963aba2e3ed589e7ebc297ba0c1b3
bd353a28886815f43fe71c561a027fdeff5cd83e17e2055c0e52bea344ae51d3
c80bd1c4a796b4d3944a097e96f384c85687daeedcdcf05cc885c8c9b279b09c
fd1b20ee5bd429046d3c04e9c675c41e9095bea70e0329bd32d7edd17ebaf68a
fe9f3b7451913f184e1f53b52a03a981dcea5564633cfcb70d01bd0aec8f30a7
fa0defdabd9fd43fe2ef1ec33574ea1af1290bd3d763fdb2bed443f2bd996d73







