- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Information Security, SIEM
By Brian Robertson, Senior Product Marketing Manager, Securonix
It is easy to understand that the more time threats dwell in your environment, the more damage they can do. The latest Securonix analyst report, “Cybersecurity Solutions for a Riskier World” shows that it takes security teams an average of 47 days to properly respond to a threat. When security analysts identify an incident, time is of the essence.
Organizations invested in SIEMs to improve the collection of data and detection of incidents. They deployed SOAR solutions to speed the response and containment of threats. However, incident investigation hasn’t seen much advancement in recent years. The process of investigating incidents is a large contributor to the amount of time it takes to resolve issues. Security analysts spend countless hours collecting the context they need to understand incidents. Gaining a clear understanding of an incident is critical to put a precise and effective action plan in place. The model below shows the steps analysts take today to gain an understanding of an incident.
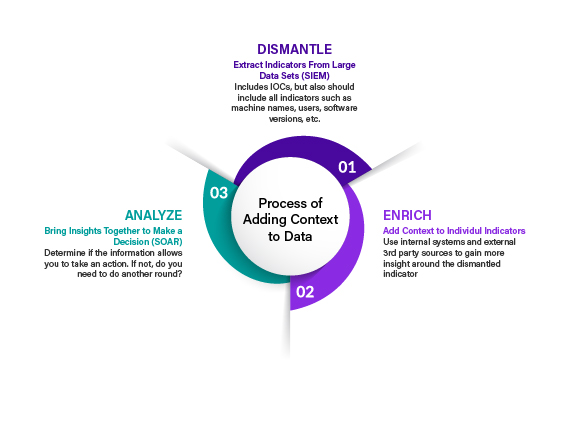
In order to effectively gain a clear understanding of an incident, security analysts need to be able to abstract key insights from large amounts of data. They then must connect those details to the issue under investigation. These connected insights must then be used to make an active decision as to what steps must be taken to mitigate the issue. The steps below outline this process as it is common today.
Phase 1: Dismantle
Security organizations look to SIEMs to extract indicators from large sets of data or data streams. Data is ingested throughout the environment to identify incidents that have the potential to be threats. To properly investigate these incidents, security analysts deconstruct down to the individual indicators involved. These indicators include things such as machine names, IP addresses, associated users, URLs, and other variables. Understanding these indicators, and their relationship with each other, is the first step in understanding the nature of the incident.
Phase 2: Enrich
Once the incident is deconstructed, data and information around each indicator must be gathered. SIEMS offer content enrichment, but often this is at the time of ingestion. When actively investigating incidents further content enrichment may be needed. To get the additional context needed, security analysts search through internal systems and external sources to find information about each indicator. Recently, security analysts look to playbooks to perform this task. However, the defining and running of playbooks is still time and resource intensive.
The issue is not that the information needed is not available. The problem is that there is too much data that resides in too many internal systems and external sources. Examples of these internal systems include security operation systems, configuration management databases, endpoint security systems, the network infrastructure, internal collaboration systems like Confluence or Jira. Security analysts may also leverage external sources. Some examples of external sources include open-source threat intelligence, subscription-based threat intelligence, threat hunting data sources, malware databases and even web-based sources like YouTube, Google Drive, and LinkedIn. The sheer number of sources of data makes it difficult to find all the related contextual data and piece it together to get an understanding of the indicator.
Phase 3: Analyze
The next step is analyzing the indicators based on the enriched data. Analyzing the indicators should provide enough of an understanding about the incident for security teams to take precise action. The art of effectively acquiring threat intelligence and context around an incident is to make sure the data is relevant. In other words, the context needs to provide insight about how the indicator can lead to a real threat. It is important to evaluate the progress of the investigation by asking yourself these questions.
- Are the indicators and context I have already actionable?
- Does the information I gathered provide a clear indication of how an attack could play out?
- If I act on the information, do I have a high level of confidence the risk will be mitigated?
Some may be surprised that often the answer to these questions is, “No”. In this case the next step is to further dismantle the incident and enrich the indicators. Security analysts, although experts in what they do, are human and may not realize the key piece of context they need resides somewhere they didn’t think of. Or they may not have considered one of the indicators as needing investigation.
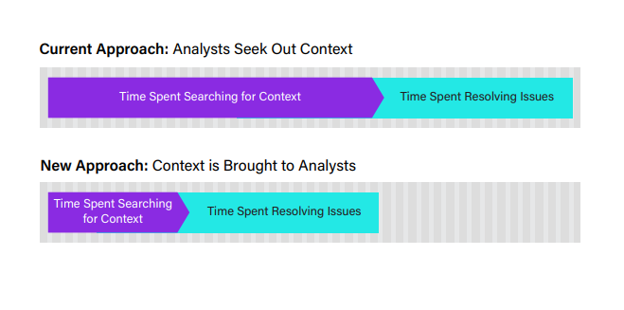
The traditional context gathering approach slows investigation
The more complex a potential threat, the more details are needed and the longer it takes to get to an actionable state. It takes time to gather the context needed and that time is exponentially increased as more repositories are queried, even with the help of playbooks. The underlying reason is that the ownership to collect the information and context around the incident’s indicators is placed on the analysts. It is a process of going and getting the context needed.
Bringing context to you
What if you could change this approach? With more incidents to contend with and a growing number of repositories that contain context, organizations need to find a new approach extracting the context they need. Instead of going out and searching through multiple sources of internal and external data, it is more efficient if we bring the data to you.
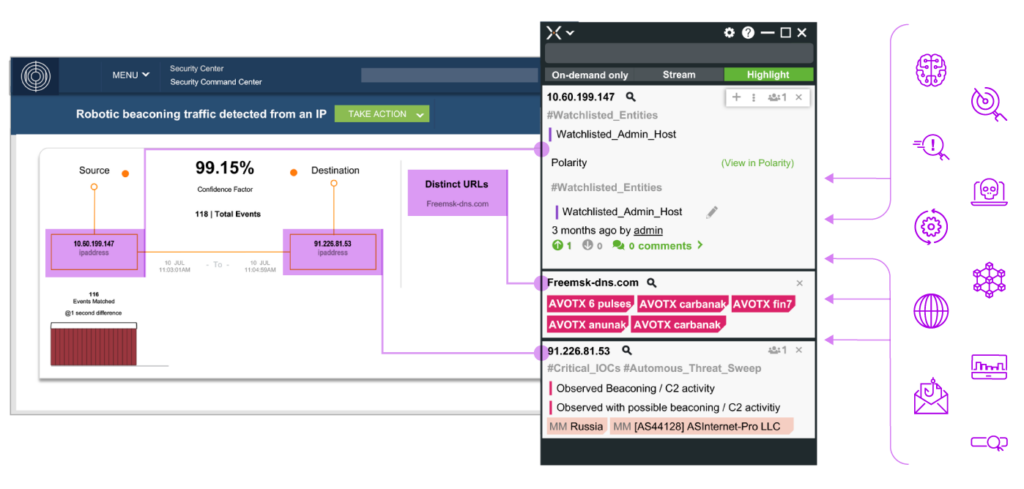
Recently, we introduced our Securonix Investigate add-on product. Securonix Investigate is designed to bring the data to the analyst instead of bringing the analysts to the data.
Securonix Investigate changes where your team spends their valuable time. Analysts move from searching through too much data in too many platforms to efficiently delivering context to the analyst as they move through their investigation. We are removing the data silos and bringing together knowledge from across the team. This capability provides a comprehensive view of the incident which leads to fast and informed decision making.
Investigate delivers an ever-present window that consolidates contextual information to enrich data presented in the Securonix interface. Securonix Investigate polls internal systems and external sources either on-demand or through streaming to display all relative context about the entities under investigation. As you move through the investigation the Securonix Investigate window updates the context so that it is directly aligned to what you are viewing within the Securonix interface.
Securonix Investigate can integrate with industry-leading solutions that include:
- Security Operation Systems
- Incident Response Systems
- Open Source/Subscription Threat Intelligence
- Threat Hunting Data Sources
- Malware Databases
- Endpoint Security Systems
- Network Infrastructure
- Others (YouTube, Google Drive, Google Search, LinkedIn…)
This new approach means that security analysts spend less time searching through multiple data repositories trying to find the needle in the haystack and more time resolving incidents. This speeds investigations and in turn delivers faster incident mitigation. Additionally, it improves analysts’ efficiency as they are able to address more incidents in less time.

Attend our upcoming webinar “Send Investigations into Hyperdrive”
Register Now