- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Insider Threat, Security Analytics
By Nagesh Swamy, Product Marketing Manager
While they may not be as numerous or widely publicized as ransomware and other external attacks, insider threats continue to be some of the most damaging that organizations contend with. According to Verizon’s 2022 Data Breach Investigations Report, external attacks outnumber insider threats by 4 to 1. However, the report cautions that, “this finding should be considered in light of the fact that insiders are adept at keeping their activities secret.”
It then observes that the number of records compromised by the average insider breach since 2008 has surpassed those of the average external attack by anywhere from 5-10 to 1, thanks to an insider’s knowledge and ability to take advantage of privilege misuse.
Insiders are difficult to detect
Insiders can inflict more damage than external threats for a number of reasons, as described in this video, “How Securonix Detects Insider Threats in Real Time.”
- Insiders are typically trusted by the organization, so they can get away with actions that would otherwise be flagged by security teams and tools.
- Unlike external actors, insiders don’t have to penetrate an organization’s network first to access sensitive systems. They already have direct access.
- Insiders know exactly where sensitive data lies and how to get to it. Many have privileged access to administrative and other accounts they can use to inflict incredible damage. This video on insider threats and the cloud describes how a user tried to gain access to an organization’s encryption key management service, which could have prevented data backups and access to data by legitimate users.
- Insiders often know how to bypass both physical and IT controls. Even insiders without any malicious intent can cause damage by providing easy access to outside attackers through misconfigurations, user error, or evasion of organizational security controls for convenience. The same video describes a situation in which an administrator struggling to update AWS cloud instances modified ingress rules to 0000, allowing access by just about anyone on the Internet, then forgot to change the rules back. This led to outside attackers gaining access to and deleting entire database instances and associated keys. The video discusses how to monitor activity to prevent these insider threats.
Too many alerts
Meanwhile, the tools organizations typically use to detect both insider and external threats generate streams of alerts based on preconfigured rules that may or may not indicate a breach in progress. Faced with so many false positives, security teams are often hard pressed to determine which alerts require follow up and which can be ignored.
In this case study, “Financial Services Organization Advances Their Insider Threat and Cloud Security” for example, a financial organization suffered alert fatigue that left it unable to discern which incidents posed a credible threat. After migrating to Securonix Next-Gen SIEM, the organization was able to get insight into its AWS cloud environment, rather than just react to a lot of false positives. Securonix UEBA enabled security analysts to build contextual information around employee activity, particularly when an employee moved to another department or left the company and detect when employees sent confidential information to their personal email accounts.
How to identify and stop insider threats
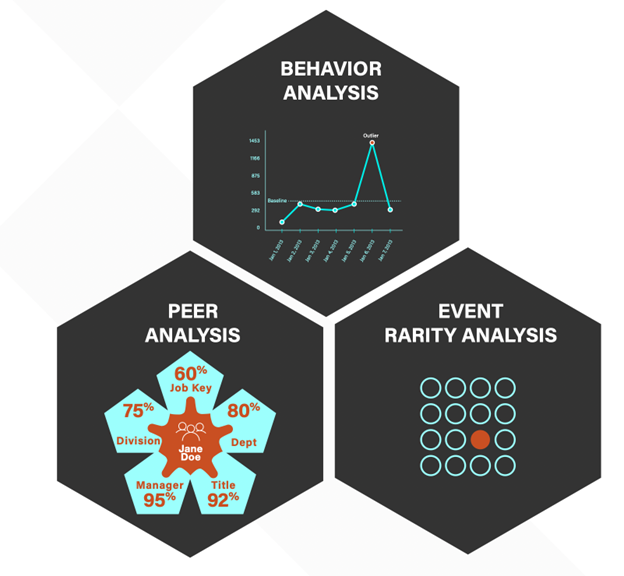
With its extensive monitoring and advanced behavioral analytics, Securonix is one of the most effective tools for detecting and addressing insider threats. Securonix generates comprehensive identity and risk profiles for every user, then tracks each user’s actions across multiple accounts and devices, identifying when their access patterns deviate from their normal behaviors. It can identify high-risk users by comparing their actions against their peers and add users to a watch list to keep a close eye on their activities. Its machine learning algorithms identify insider attacks that span multiple alerts using threat models that map to both the MITRE ATT&CK and US-CERT frameworks. Securonix comes with an insider threat package that tracks insider credential sharing, data egress, data snooping, and expense fraud, and includes a lot of prebuilt content. This solution brief, “Insider Threat Detection and Response” provides more information on how Securonix detects and stops insider attacks.
Investing in your organization
The ROI Securonix can achieve can be considerable, as this white paper, “Justify Your Insider Threat Program,” points out. It can be measured in the volume and value of information saved from exfiltration, which is typically higher with an insider threat. Securonix significantly reduces the time required to detect and respond to insider threats. By successfully detecting exfiltration attempts, Securonix provides information that allows organizations to take successful legal action against, discipline, or terminate inside threat actors.
Ransomware and other external threats typically get most of the news and attention when it comes to cybersecurity, but failing to be vigilant against insider threats can expose your organization to substantial data loss, theft, and reputational damage. Legacy security tools can overwhelm security teams with false positives, but by using constant monitoring and behavioral analytics, a next generation SIEM can slash false positives and catch insiders in the act.


