- Why Securonix?
- Products
-
- Overview
- 'Bring Your Own' Deployment Models
-
- Products
-
- Solutions
-
- Monitoring the Cloud
- Cloud Security Monitoring
- Gain visibility to detect and respond to cloud threats.
- Amazon Web Services
- Achieve faster response to threats across AWS.
- Google Cloud Platform
- Improve detection and response across GCP.
- Microsoft Azure
- Expand security monitoring across Azure services.
- Microsoft 365
- Benefit from detection and response on Office 365.
-
- Featured Use Case
- Insider Threat
- Monitor and mitigate malicious and negligent users.
- NDR
- Analyze network events to detect and respond to advanced threats.
- EMR Monitoring
- Increase patient data privacy and prevent data snooping.
- MITRE ATT&CK
- Align alerts and analytics to the MITRE ATT&CK framework.
-
- Industries
- Financial Services
- Healthcare
-
- Resources
- Partners
- Company
- Blog
Insider Threat
By Oliver Rochford, Applied Research Director, Threat Labs, Securonix
Cyber attacks often come from employees or contractors with legitimate access to an organization’s network and applications. Insider threat actors are common — for example, Verizon found that 62% of system intrusion incidents resulted from compromised partners — but they are also difficult to prevent because insiders already have access to your environment and require an inherent level of trust to complete their job functions. They also know where to locate sensitive data and often have elevated access to critical information.
Attacks from insiders, intentional or accidental, are costly. These attacks lead to loss of confidentiality, intellectual property, and money. According to Ponemon Institute’s 2020 Cost of Insider Threats study, the average annual cost of internal data breaches is $11.45 million.
Three types of insider threats should be on every organization’s radar:
- Negligent insiders: Employees or contractors who expose data accidentally due to poor security practices.
- Complacent insiders: Employees or contractors that intentionally ignore security policies.
- Malicious insiders: Employees or contractors who intentionally compromise data.
Negligent and complacent insiders are most common; however, several factors spawned by the COVID-19 pandemic, such as the Great Reshuffle, have complicated the threat landscape. A different kind of malicious insider threat is on the rise: insider collusion.
What is accomplice-based cybercrime?
Insider collusion fuels accomplice-based cybercrime, consisting of employees offering their legitimate credentials to initial access brokers (IABs) for money, and in the case of ransomware groups a percentage of the payout. IABs specialize in breaching companies and selling access to other cybercriminals. Brokers typically target large corporations in the United States, Canada, Australia, and the United Kingdom that generate over $100 million in revenue, as these make lucrative victims able to pay high ransoms.
A recent survey conducted by Hitachi ID found that 65% of employees were approached to help hackers establish initial access to corporate networks between December 7, 2021, and January 4, 2022. Brokers initiated contact with insiders through various means, including email, social media, and phone. They also advertise on underground forums and dark web marketplaces.
Rogue insiders are motivated for several reasons to sell their identities to cybercriminals. Some employees are disgruntled by pandemic layoffs and increases in the cost of living. There’s also the opportunity to receive a life-changing sum of money. To provide just one example, Demonware, a Nigerian threat actor, offered its potential ransomware accomplices 40% of an expected $2.5 million payout. Accomplices can receive payment anonymously through cryptocurrency, making their participation difficult to trace. In addition, there is also an element of plausible deniability, as insiders can claim to have been hacked, or even willingly click on a phishing email sent by their accomplices.
Implications of insider collusion
As cybersecurity defenses have become stronger, the tactics attackers use to compromise corporate data environments have also become more sophisticated. The best way to beat defenses is not to face them in the first place, and so cybercriminals are aggressively soliciting employees and incentivizing them with large sums of money.
Insider attacks often lack the types of indicators of compromise that an external attacker frequently leaves behind, such as suspicious processes or malicious malware, making detection a far more challenging proposition. Insiders also frequently have detailed knowledge about the digital infrastructure and security measures a business has deployed, enabling them to act as a scout for cybercriminal accomplices and help them further evade detection. Security analysts must instead focus on the more difficult tactics, techniques, and procedures (TTPs) employed by attackers. For insiders in particular, this means identifying suspicious behavior. TTPs are harder to detect for defenders, but that means that cyber attacks can be detected earlier, and if done well, more importantly means that any attacker will find it much more difficult to act stealthily in the future.
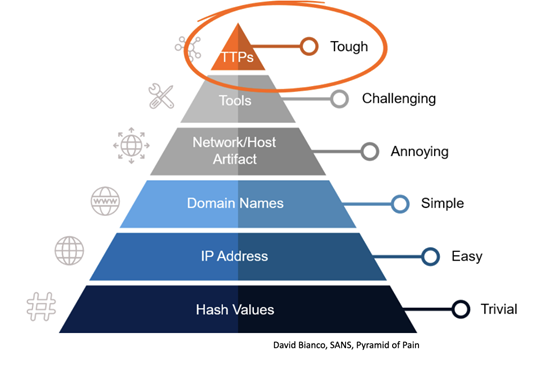
Accomplice-based ransomware attacks also make other security controls less effective and more difficult to implement. For example, restricting malicious use through application allow-listing only works if an attacker doesn’t have privileged access. Therefore, security analysts have to supplement incident response, forensic investigation, and threat hunting with in-depth asset and user context to uncover who’s using which tools when, how, and why.
In addition, enhancing security awareness among employees sounds advantageous, but can quickly turn out to be counterproductive. Better training can actually teach malicious insiders what to avoid and how to masquerade themselves as victims of cyberattacks more effectively.
How to protect your organization
Defending your network against paid insiders is challenging, but possible. Here are steps you can take to develop a proactive insider threat mitigation program.
Adapt your security program
Implement Zero Trust best practices, including least-privilege access, multi-factor authentication, and network segmentation to help verify every user and device on your network. Conduct routine threat hunting to preempt insider attacks and assume your threat detection technologies haven’t caught every instance of suspicious activity on your network.
In addition to technology, effective insider threat programs also focus on people and processes. Developing an insider threat working group (ITWG) is a great way to bring together technical and non-technical representatives from various departments, like HR, Legal, IT, and Compliance, to advise employees on security best practices and protect against insider threats.
Improve detection capabilities
Deploy a security technology stack that covers multiple attack vectors and blends detection approaches. Indicators of compromise aren’t a reliable tool for detecting insider threats, therefore organizations should use behavioral analysis to augment traditional detection methods. Securonix User and Entity Behavior Analytics uses machine learning and artificial intelligence to help organizations baseline behavioral patterns to uncover anomalous activity.
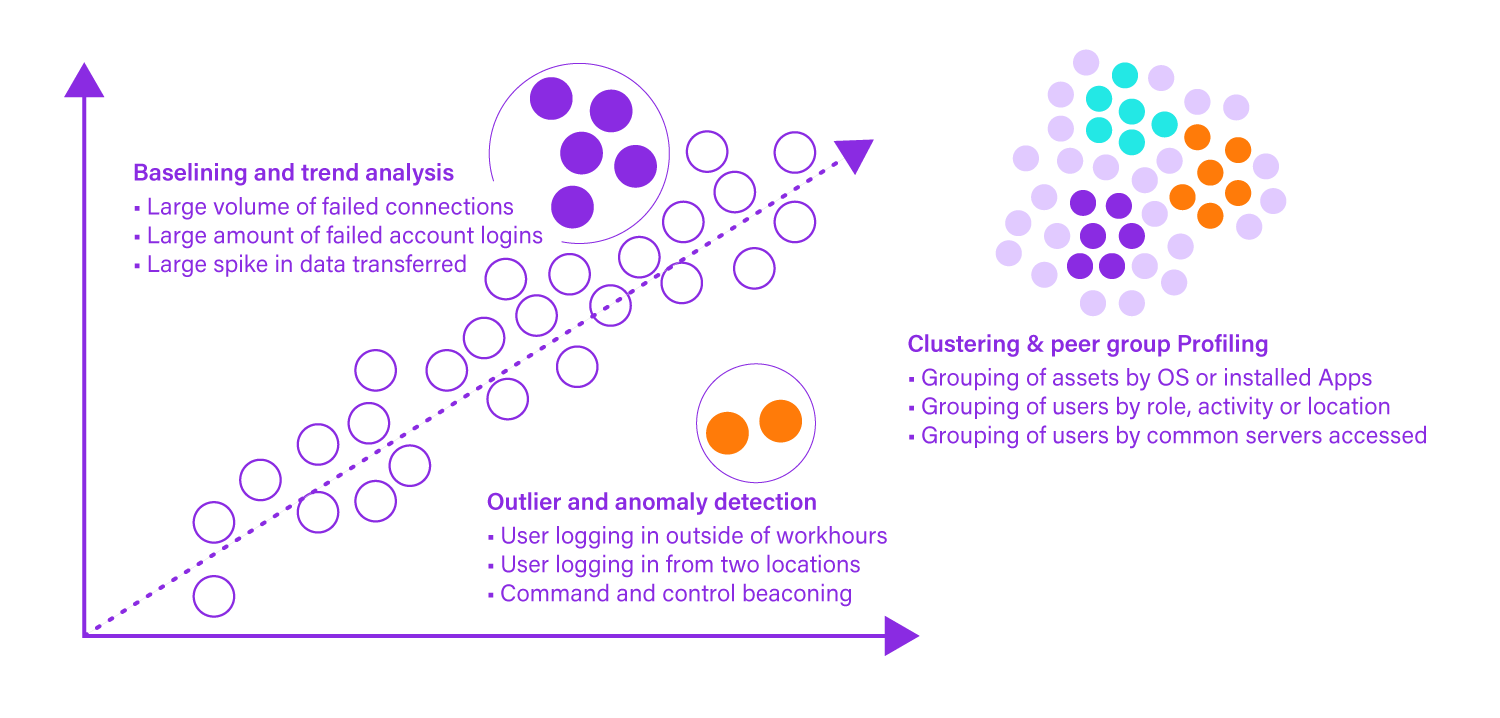
Behavioral analysis enables organizations to spot early warning signs of insider threats, including remote network access gained outside of office hours, multi-region authentication, and employees retrieving sensitive data unrelated to their role.
Learn how Securonix helps leading organizations stop and prevent insider threats with advanced behavioral analytics and Next-Gen SIEM.



