By Oleg Kolesnikov, Securonix Threat Research Team
Introduction
In August 2017, we learned of new attacks by a persistent malicious cyber threat actor known by the name of Carbanak aka FIN7 [1]. The most recent attack variants have been targeting mainly chain restaurants, hospitality, and casino industry in the US for financial information/POS/credit card data.
Securonix Threat Research Team has been actively investigating and closely monitoring attacks associated with this high-profile continuously evolving malicious cyber threat actor to help our customers prevent, detect, and mitigate/respond to the attack.
Based on the practical security analysis of this attack we performed in our lab, here is a summary of what we currently know and our recommendations on some possible mitigations and Securonix predictive indicators/security analytics that can be used to detect the current and potential future attack variants by this malicious cyber threat actor.

Figure 1: Carbanak/FIN7 Attack – Initial Infiltration – Malicious Word File
Summary
Here is a summary of some of the key technical details about this high-profile attack.
- Infiltration vector(s): The primary attack vector is phishing e-mails containing specially crafted Microsoft Word documents/RTF attachments with macro/OLE content that cause malicious obfuscated Javascript or VB stagers to be dropped and executed;
- Capabilities: The attacks by this malicious cyber threat actor leverage a number of different attack variants/payloads/tools e.g. DNS tunneling/staging/C2, ggldr scripts receiving commands from Google Sheets, Google Apps Script, and Google Forms, commodity backdoors–bateleur JS dropped from macros etc. [3].
Some of the capabilities leveraged by this malicious cyber threat actor include custom command and powershell/stager execution, POS monitoring, keylogging, HTTP form grabbing, file transfers, proxying, VMM/sandbox detection, desktop video capture etc. This malicious cyber threat actor has been active for more than a year and has been constantly evolving its capabilities over time;
- Observed Artifact Hash Values: There is a large number of attack/artifact variants associated with Carbanak/FIN7 malicious cyber threat actor attacks and new variants appear regularly. Some of the recent artifact values include:
MD5:
6e9408c338e98a8bc166a8d4f8264019
0f556e5099e497b97865cff0a585cb29
37eaa3b25ccb4869faa2a111d4ecb3c2
2828ea78cdda8f21187572c99ded6dc2
fb6f9e615ca2d7585cd8381e43e9bc01
184efc90afea91922eb48da3eb9af050
188f261e5fca94bd1fc1edc1aafee8c0
6e9408c338e98a8bc166a8d4f8264019
SHA256:
803009b5cf8d663a2fa3e20651cbdd57da25908366d886c2eebc1a4bf7dfc3f0
75378b418f19c2b6fbac8a9651646bd4184570c7f1dfe698f6d231458b700f1f
2781526f6b302da00661b9a6a625a5a6ecf4ffccafa61202e9b0e9b61b657867
c357396ca82fdcd6b6f46b748f2b6941051dbc81be5326cf9548e6e95507af7c
ffebcc4d2e851baecd89bf11103e3c9de86f428fdeaf0f8b33d9ea6f5ef56685
and a number of others.

Figure 2: Carbanak/FIN7 Attack – Execution
Behaviors – Carbanak/FIN7 Host Activity
Some of the commands ran by this malicious cyber threat actor on the target include:

The commands can be used in the Securonix Rule-based policies leveraging EDR log sources/data sources (see below).
Detection – Sample Spotter Search Queries
Please find below sample Spotter search queries to assist with detection of the existing infections:
- Network Traffic (Proxy/Firewall outbound)
(rg_category = “Proxy” OR rg_category = “Firewall” or rg_category = “DNS” ) AND (ipaddress = 198.100.119.6 or ipaddress = 94.140.120.132 or ipaddress=176.101.223.101 or ipaddress=185.86.151.210 or ipaddress=138.201.44.10 or ipaddress=176.101.223.101 or ipaddress=176.101.223.100 or ipaddress=204.155.30.100 or ipaddress=94.140.120.132 or ipaddress=94.140.120.132 or ipaddress=94.140.120.132 or ipaddress=176.101.223.100 or ipaddress=179.43.140.85 or ipaddress=95.215.44.12 or ipaddress=95.215.47.105 or ipaddress=192.99.14.211 or ipaddress=80.84.49.61 or ipaddress=95.215.46.229 or ipaddress=107.181.246.189 or ipaddress=80.84.49.66 or ipaddress=95.215.46.234 or ipaddress=148.251.18.75 or ipaddress=138.201.44.4 or ipaddress=81.17.28.124 or ipaddress=95.215.45.94 or ipaddress=179.43.140.85 or ipaddress=89.163.248.8 or ipaddress=95.215.46.249 or ipaddress=80.83.118.233 or ipaddress = 62.210.25.121 or ipaddress=95.215.46.221 or ipaddress=104.250.138.197 or ipaddress=212.129.36.175 or ipaddress=179.43.133.34 or ipaddress=89.163.248.6 or ipaddress=95.215.44.94)
#2 – (rg_category = “Proxy” OR rg_category = “Firewall” or rg_category = “DNS” ) AND (destinationhostname contains “true-deals.com” or destinationhostname contains “strikes-withlucky.com” or destinationhostname contains “rescsovwe.com” or destinationhostname contains “proslr3.com”)
#3 – rg_category = “DNS” and destinationhostname contains “aaa.stage.”
Detection – Securonix Behavior Analytics/Security Analytics
Here is a high-level summary of some of the relevant Securonix predictive indicators to increase the chances of early detection of this and potentially other future variants of attacks carried out by this malicious cyber threat actor on your network:

Figure 3: Carbanak/FIN7 Attack Process Activity
#1 – Suspicious Process/Service Activity Anomalies
- Suspicious Process Activity Rare Process/MD5 For User/Host Anomaly
- This should help detect unusual Winword, wscript, and sdbinst activity mentioned above (see Figure 3);
- Suspicious Process Activity Unusual Parent-Child Relationship For User/Host Anomaly

Figure 4: Carbanak/FIN7 More Attack Staging/Process Activity
- Suspicious Process Activity Command Line Arguments Anomaly
- Suspicious Registry Activity Autorun Changes Anomaly
- Suspicious Registry Activity Shim Database Changes Anomaly
- Note that this may require adding entries to the sysmon configuration to ensure the following registry keys are monitored:
- “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Custom”
- “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\InstalledSDB”

Figure 5: Carbanak/FIN7 Attack JS Stager
- Suspicious Process Activity Dynamic Script File Create Anomaly
- Suspicious Process Activity Unusual Network Connection Anomaly
- Suspicious Process Activity Unusual Scheduled Task Anomaly
#2 – Suspicious Network Activity Anomalies
- Suspicious Network Activity DNS IN TXT Query Volume Anomaly (Peak);
- Suspicious Network Activity DNS IN A Query Volume Anomaly (Peak);
- Suspicious Network Activity DNS Query Content Beacon Anomaly (Targeted);
- Unusual contents of dns.qry.name & dns.a (Targeted);
- Suspicious Proxy Activity Non-SSL/TLS App On SSL/TLS Port Discrepancy Anomaly
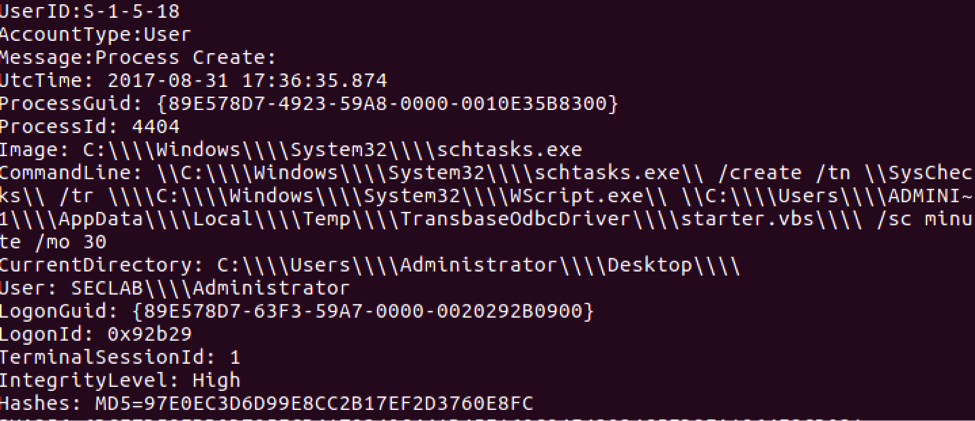
Figure 6: Carbanak/FIN7 Attack Scheduled Task Execution
If you have any further questions regarding this high-profile threat and how Securonix can be leveraged to detect the behaviors associated with the threat, please contact the Securonix Threat Research Team at [email protected].
References
[1] James T. Bennett, Barry Vengerik. Behind the CARBANAK Backdoor. FireEye Threat Research Blog. 12 June 2017.[2] Matthew McWhirt, Jon Erickson, DJ Palombo . To SDB, Or Not To SDB: FIN7 Leveraging Shim Databases for Persistence. FireEye Threat Research Blog. 3 May 2017.
[3] Matthew Mesa, Darien Huss. FIN7/Carbanak threat actor unleashes Bateleur JScript backdoor. Proofpoint Threat Research Blog. 31 July 2017.