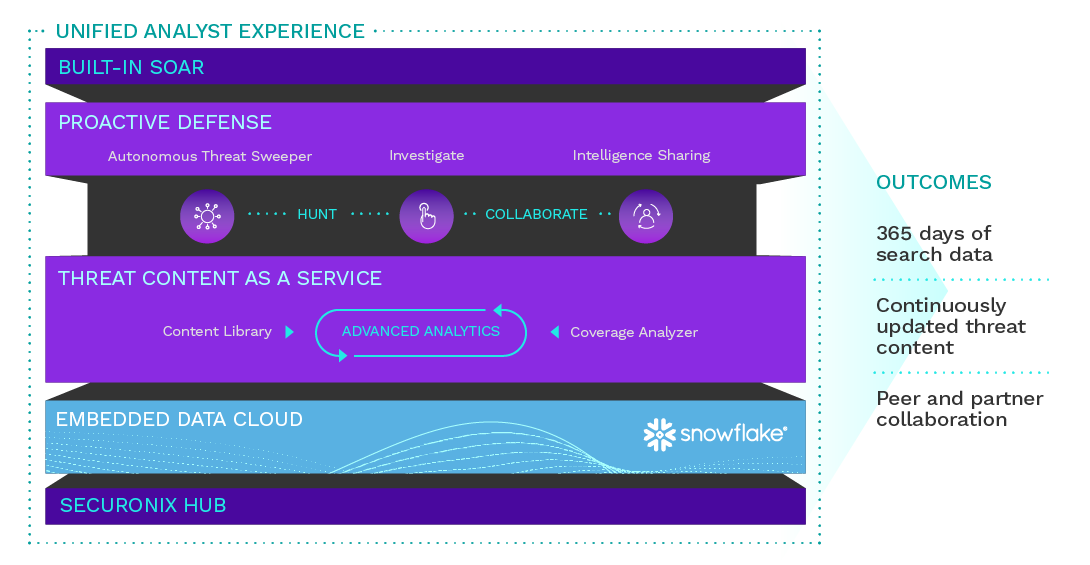
IntroducingUnified Defense SIEM
Embedded Data Cloud
Threat Content-as-a-Service
Proactive Defense
Unified TDIR Experience
Embedded Data Cloud
Threat Content-as-a-Service
Proactive Defense
Unified TDIR Experience
-
Former National Cyber Director Chris Inglis Joins Securonix’s Newly Formed Strategic Advisory Board
Diverse Leadership Group of Distinguished Industry Veterans Brings Valuable Public and Private Sector Experience to Help Guide Growth and Expansion for Cloud-Native Security Analytics Leader
Read Press Release -
Securonix Launches Industry’s First Unified Defense SIEM Platform
Best-in-class Threat Defense
Read Press Release -
Gartner® Peer Insights™ 2023 Customers’ Choice for Security Information and Event Management
Securonix Named a Customers’ Choice
Read the Report -
Gartner® 2022 Critical Capabilities for Security Information and Event Management
Securonix Among Three Highest Scoring Vendors For All Use Cases
Read the Report
Unified Defense SIEM Platform
Get best-in-class threat defense with a SIEM that unifies threat detection, investigation, and response (TDIR) on Snowflake’s Data Cloud.
-
 Scalable
Scalable
Data LakeGain fast access to one year of hot data for investigations, threat hunting, and response.
-
 Threat
Threat
Content-as-a-serviceUnlock broad threat coverage through continuously curated and delivered threat content that reduces false positives.
-
 Proactive
Proactive
DefenseHarness the power of intelligence produced and shared by their peers and partners.
-
 Unified
Unified
TDIR ExperienceStreamline the analyst experience to deliver detection, investigation, and response in a single interface.
Flexible Deployment for Every Organization
-
 Securonix SaaS
Securonix SaaSSecuronix delivers an analytics-driven SIEM and UEBA as a pure cloud solution without compromise.
-
 Bring Your Own Cloud
Bring Your Own CloudKeep your data in your cloud environment while unlocking powerful threat detection and response.
-
 Managed Service
Managed ServiceSecuronix solution powers and is delivered by 70+ MSSP and MDR partners globally.

Customer Spotlight: Alberta Health Services
Alberta Health Services reduces false positives by 90% with Securonix.

The Need
Alberta Health Services experienced alert fatigue from too many false positives while spending 2-3 hours a day on SIEM maintenance and tuning issues.
The Solution
Alberta Health Services reduced false positives by 90% compared to their previous SIEM solution and offloaded maintenance so the team could focus on detection and response.

Customer Spotlight: LeaseLock
LeaseLock won more business by improving detection and compliance for PII and financial data.

The Need
LeaseLock needed to build customer trust through stronger data privacy and compliance reporting. They chose the Securonix Next-Gen SIEM to centralize and improve their security operations.
The Solution
LeaseLock reduced manual security investigations from hours to minutes while improving compliance and reporting. They won new business with their stronger security posture and gained the ability to detect signatureless threats from insiders.

Global Infrastructure Leader Gains Multi-Cloud Visibility and Threat Detection
Removed silos and reduced complexity by analyzing all logs within Snowflake and only paid for compute resources used.

The Need
The global infrastructure leader’s legacy SIEM lacked the ability to scale, multi-cloud visibility, and was growing in cost. With ongoing acquisitions, they needed more robust threat detection capabilities to meet their business needs.
The Solution
The security team saw the immediate benefits of keeping all their data in one place using their Snowflake instance and leveraging Securonix Next-Gen SIEM to detect and respond to security threats. They gained multi-cloud flexibility and industry-leading security.

Holding Company Stops Phishing and Data Exfiltration with a Single Platform
Centralized visibility and threat detection across multiple business units without requiring a large security team.

The Need
The Holding Company needed to consolidate its security tools across all its business units to catch insiders and advanced attacks.
The Solution
Securonix Next-Gen SIEM with powerful UEBA capabilities reduced noise by taking thousands of possible phishing alerts to single digits. Additionally, they could detect data exfiltration attempts without a large security team.

Ready for a Demo?
Securonix collects massive volumes of data in real time, detects advanced threats using innovative machine learning algorithms, enables you to quickly investigate the alerts that matter the most, and provides actionable security intelligence for an automated response.
Thanks for contacting us! We will get in touch with you shortly.
By clicking submit you agree to our Privacy Policy.
Thanks for contacting us! We will get in touch with you shortly.
By clicking submit you agree to our Privacy Policy.
Thanks for signing up!
By clicking submit you agree to our Privacy Policy.
